1. What steps would you take to handle a...
PROGRAMMING
Converting a PPK (PuTTY Private Key) file to a...
Here are the key benefits of gRPC: High Performance:...
The login functionality is a critical component of any...
How and where is data stored? How is data...
The following best practices for Amazon S3 can help...
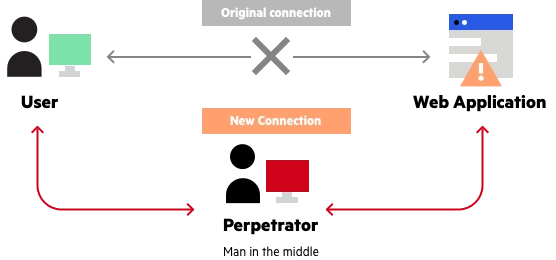
A Man-in-the-Middle (MITM) attack refers to a situation where...
What is SAML? SAML, which stands for Security Assertion...
Straight-Through Processing (STP) is a method used in various...
Ensuring the security of your source code is crucial...